Hyrax - User Identification (Authentication): Difference between revisions
| Line 49: | Line 49: | ||
This will expose the web application "opendap" (aka Hyrax) through Apache. Make sure that the AJP URLs both point to your deployment of Hyrax. | This will expose the web application "opendap" (aka Hyrax) through Apache. Make sure that the AJP URLs both point to your deployment of Hyrax. | ||
==== Taking advantage of Apache Logging ==== | |||
Often when authentication is needed, it is also necessary to log ''who'' has logged in and ''what'' they have accessed. Apache has a very flexible logging system; that can tell you what users asked for, where they came from, and when they made the request - among other things. For specific authentication technologies it may also be possible to log specific information about UIDs, etc. See the sections below for information on configuring Apache's log to record that kind of technology-specific data. | |||
==== Add SSL Capabilities to Apache ==== | ==== Add SSL Capabilities to Apache ==== | ||
Revision as of 19:29, 10 December 2014
Overview
This document is intended to help those that have been asked to deploy Hyrax into an environment where authentication of users is required. In many such cases Hyrax will be integrated into an existing instance of the Apache Web server (httpd) where authentication services are already configured and in use. In other cases people will be setting up a standalone instance of Tomcat and will be needing to configure it to use one of the supported authentication services. This document means to address both situations.
Terms
- Authentication
- This is the process of confirming the identity of the user. The end result is a User ID (uid or UID) which may be accessed by the software components via (both?) the Apache API (mod_*) and the Java ServletAPI (Tomcat servlets) used to trigger authorization policy chains or may be logged along with relevant request information.
- Identity Provider (IdP)
- Also known as an Identity Assertion Provider, an Identity Provider (IdP) is a service that provides authentication and identity information services. An IdP is a kind of provider that creates, maintains, and manages identity information for principals and provides principal authentication to other service providers within a federation, such as with web browser profiles.
- Service Provider (SP)
- A Service Provider (SP) is a Web Service that utilizes an IdP service to determine the identity of it's users. Or more broadly, a role donned by a system entity where the system entity provides services to principals or other system entities.
With respect to this document Hyrax/Tomcat, and Hyrax/Tomcat/Apache each become part of an SP through the installation and configuration of software components such as mod_shib (shibboleth) .
See Service Providers, Identity Providers & Security Token Services explained for more.
Apache httpd Authentication Services Configuration
There are many authentication methods available for use with our friend httpd snd each of the three illustrated here has a unique installation and configuration activity. There are some common changes that must be made to the Tomcat configuration regardless of the authentication method employed by Apache. We'll cover those first and then examine LDAP, Shibboleth, and NASA URS IdP configurations for Apache httpd.
- NB
- If you are deploying Hyrax with an existing Apache service then it is likely that all you have to do is configure httpd and Tomcat to work together and define and then define a security constraint for httpd that enforces a login requirement (valid-user) for Hyrax.
Tomcat <=> httpd
First: Configure Apache httpd and Tomcat to work together
In this part we configure Tomcat and Apache httpd to work together so that httpd can provide proxy and authentication services for Hyrax.
Configure Apache
In /etc/httpd/conf.d create a file called hyrax.conf . Edit the file and add following:
<Proxy *>
AddDefaultCharset Off
Order deny,allow
Allow from all
</Proxy>
ProxyPass /opendap ajp://localhost:8009/opendap
ProxyPassReverse /opendap ajp://localhost:8009/opendap
This will expose the web application "opendap" (aka Hyrax) through Apache. Make sure that the AJP URLs both point to your deployment of Hyrax.
Taking advantage of Apache Logging
Often when authentication is needed, it is also necessary to log who has logged in and what they have accessed. Apache has a very flexible logging system; that can tell you what users asked for, where they came from, and when they made the request - among other things. For specific authentication technologies it may also be possible to log specific information about UIDs, etc. See the sections below for information on configuring Apache's log to record that kind of technology-specific data.
Add SSL Capabilities to Apache
This step is not absolutely necessary, but it's quite likely you will want to do this, particularly if you're going to use https to access the tomcat servlet engine running the Hyrax front-end. If you use https in the AJP configuration as shown in the next section, you will need to set up Apache to support https even if users don't access the server with that protocol (because internally, some of the server's less performance intensive functions work by making calls to itself, and those will use https if you've set up tomcat to use https with AJP). However, the configuration is very simple.
First, make sure you have mod_ssl installed. For CentOS 6, use sudo yum install mod_ssl
Next make the needed certs. Here's how to make and install a self-signed cert for CentOS 6:
# Generate private key
openssl genrsa -out ca.key 2048
# Generate CSR
openssl req -new -key ca.key -out ca.csr
# Generate Self Signed Key
openssl x509 -req -days 365 -in ca.csr -signkey ca.key -out ca.crt
# Copy the files to the correct locations
cp ca.crt /etc/pki/tls/certs
cp ca.key /etc/pki/tls/private/ca.key
cp ca.csr /etc/pki/tls/private/ca.csr
Configure httpd to use the newly installed certs and restart:
- The configuration file is in: /etc/httpd/conf.d/ssl.conf
- Edit SSLCertificateFile /etc/pki/tls/certs/ca.crt
- ... and SSLCertificateKeyFile /etc/pki/tls/private/ca.key
- and then restart: sudo /usr/sbin/apachectl restart
NB: More complete instructions can be found here: http://wiki.centos.org/HowTos/Https
Configure Tomcat (Hyrax)
The primary result of the Apache authentication (the uid string) must be correctly transmitted to Tomcat. On the Tomcat side we have to open the way for this by configuring a AJP Connector object. This is done by editing the file:
- $CATALINA_HOME/conf/server.xml
Edit the server.xml file, and find the AJP Connector element on port 8009. It should look something like this:
<Connector port="8009" protocol="AJP/1.3" />
This line may be "commented out," with <!-- on a line before and --> on a line after. If so, remove those lines. If you cannot find the AJP connector element, simply create it from the code above.
- In order to receive authentication information from Apache, you must disable Tomcat's native authentication. Set the tomcatAuthentication attribute to "false" - see below for an example.
- If your Apache web server is using SSL/HTTPS (and it should be), you need to tell Tomcat about that fact so that it can construct internal URLs correctly. Set the scheme attribute to "https" and the proxyPort attribute to "443" - see below for an example.
- For increased security, disable access to the connector from anywhere but the local system. Set the address attribute to "127.0.0.1" - see below for an example.
When you are finished making changes, your connector should look something like this:
<Connector
port="8009"
protocol="AJP/1.3"
redirectPort="443"
scheme="https"
address="127.0.0.1"
enableLookups="false"
tomcatAuthentication="false"
/>
- port
- The Connector will listen on port 8009.
- protocol
- The protocol is AJP/1.3.
- redirectPort
- Secure redirects to port 443 which is the nominal Apache HTTPS port, rather than the default 8443 which is nominally directed to Tomcat.
- scheme
- Ensure that scheme is HTTPS, this is a best practice and is simple enough if the server is already configured for HTTPS. If you are not going to utilize HTTPS elsewhere in the server you'll either need to set the value of scheme to "http" or you'll need to enable and configure the server for TLS/SSL transport.
- address
- The loopback address (127.0.0.1) ensures that only local requests for the connection will be serviced.
- enableLookups
- A value of true enable DNS look ups for Tomcat. This means that web applications (like Hyrax) that will see the client system as a host name and not an IP address. Set this to false to improve performance.
- tomcatAuthentication
- A value of false will allow the Tomcat engine to receive authentication information (the uid and in some cases other attributes) from Apache httpd. A value of true will cause Tomcat to ignore Apache authentication results in favor of it's own.
Restart Tomcat to load the new configuration. Now the Tomcat web applications like Hyrax should see all of the Apache authentication attributes. (These can be retrieved programmatically in the Java sServlet API by using HttpServletRequest.getRemoteUser() or HttpServletRequest.getAttribute("ATTRIBUTE NAME"). Note that HttpServletRequest.getAttributeNames() may not list all available attributes – you must request each attribute individually by name.)
Second: Configure Apache httpd to authenticate
Once Tomcat and Apache httpd are working together all that remains is to configure a security restraint on the Hyrax web application and specify the authentication mechanism which is to used to identify the user.
While the details of the Apache security constraints differ somewhat from one IdP to the next what is consistent is that you will need to define a security constraint on Hyrax inside the chain of httpd.conf files. The most simple example, that you want all users of the Hyrax instance to be authenticated, might look something like this:
# This is a simplified generic configuration example; see the sections below for the real
# examples for LDAP, Shibboleth or URS/OAuth2
<Location /opendap>
AuthType YourFavoriteAuthTypeHere
require valid-user
</Location>
Where the require valid-user attribute requires that all accessors be authenticated and where YourFavoriteAuthTypeHere would be something like Basic, UrsOAuth2 or shibboleth.
Complete examples for LDAP, URS/OAuth2, and Shibboleth IdPs are presented in the following sections.
LDAP
LDAP (mod_ldap, mod_authnz_ldap)
NB: You must configure Apache and Tomcat (Hyrax) to work together prior to completion of this section.
In order to get Apache httpd to use LDAP authentication you will have configure an Apache security constraint on the Hyrax web application. For this example we will configure Apache to utilize the Forum Systems public LDAP server
- All user passwords are password.
- Groups and Users:
- mathematicians
- riemann
- gauss
- euler
- euclid
- scientists
- einstein
- newton
- galieleo
- tesla
- mathematicians
Create and edit the file /etc/httpd/conf.d/ldap.conf.
Add the following at the end of the file:
# You may need to uncomment these two lines...
# LoadModule ldap_module modules/mod_ldap.so
# LoadModule authnz_ldap_module modules/mod_authnz_ldap.so
# You may want to comment out this line once you have it working.
LogLevel debug
<Location /opendap >
Order deny,allow
Deny from all
AuthType Basic
AuthName "Forum Systems Public LDAP Server- Login with user id"
AuthBasicProvider ldap
AuthzLDAPAuthoritative off
AuthLDAPURL ldap://ldap.forumsys.com:389/dc=example,dc=com
AuthLDAPBindDN "cn=read-only-admin,dc=example,dc=com"
AuthLDAPBindPassword password
AuthLDAPGroupAttributeIsDN off
ErrorDocument 401 "Please use your username and password to login into this Hyrax server"
Require valid-user
Satisfy any
</Location>
Restart Apache httpd and you should now need to authenticate to access anything in /opendap
Shibboleth (mod_shib)
Shibboleth (mod_shib)
NB: You must configure Apache and Tomcat (Hyrax) to work together prior to completion of this section.
The Shibboleth wiki provides excellent documentation on how to get Shibboleth authentication services working with Tomcat. This is primarily an Apache httpd activity.
Basically you need to follow the instructions for a Native Java Install and remember - Hyrax does not use either Spring or Grails.
Installation
The logical starting point for this is with the Native Java SP Installation:
But as far as the organization of the work is concerned it is really the last page you need to process, as it will send you off to do a platform dependent Shibboleth Native Service Provider for Apache installation which needs to be completed, working, and configured before you'll return to the Native Java SP Installation to enable the part where Tomcat and mod_shib pass authenticated user information into Tomcat.
The document path on the Natvie Java Install wiki page will send you off to do Shibboleth Native Service Provider installation which is platform dependent:
- https://wiki.shibboleth.net/confluence/display/SHIB2/Installation
- Install a Native Service Provider on your target system.
- In the initial testing section for Linux they suggest accessing the Status page https://localhost/Shibboleth.sso/Status, but you may have to use the loopback address to be able to do so: https://127.0.0.1/Shibboleth.sso/Status
Return to the Native Java SP Installation and complete the instructions there.
Configuration
Once the SP installation is completed go to the Native SP Configuration page:
Read that page and then follow the link to the instructions for Apache:
Follow those instructions.
- Do not be confused by the section Making URLs Used by mod_shib Get Properly Routed. While you must add this Location directive to "reveal" the shibboleth module to the world don't think the URL https://yourhost/Shibboleth.sso is a valid access point to the module. That URL may always return a Shibboleth error page even if mod_shib and shibd are configured and working correctly.
- Read and understand the section Enabling the Module for Authentication
The Shibboleth instructions should have had you add something like this:
<Location /opendap>
AuthType shibboleth
ShibRequestSetting requireSession 1
require valid-user
</Location>
to httpd.conf. This will require users to authenticate to access any part of Hyrax which may be exactly what you want. If you want more fine grained control you may want use multiple Location elements with different require attributes. For example:
<Location /opendap>
AuthType shibboleth
ShibCompatWith24 On
require shibboleth
</Location>
<Location /opendap/AVHRR>
AuthType shibboleth
ShibCompatWith24 On
ShibRequestSetting requireSession 1
require valid-user
</Location>
</apache>
In this example the first Location establishes Shibboleth as the authentication tool for the entire /opendap application path, and enables the Shibboleth module over the entire Hyrax Server.
- Since there is no
ShibRequestSetting requireSession 1line it does not require a user to be logged in order to access the path. - The
require shibbolethcommand activates mod_shib for all of Hyrax.
The second Location states that only valid-users may have access "/opendap/AVHRR" URL path.
- The
require valid-usercommand requires user authentication. - The
AuthTypecommand is set toshibbolethso mod_shib will be called upon to perform the authentication.
For more examples and better understanding see the Apache Configuration section of the Shibboleth wiki.
URS
URS OAuth2 (mod_auth_urs)
URS/OAuth2 is a redirect authentication flow where client applications requesting an authenticated resource are redirected to a central URS authentication point, authenticated, and redirected back to their requested resource. This way user credentials, however they may be exchanged, are only ever exchanged with a single trusted service.
In order to get a new instance of mod_auth_urs running you will need application credentials for the new instance from the URS system. Because each registered application is linked to a single redirectUrl, each different running instance of mod_auth_urs will need to be registered in order to successfully have the server redirect clients back from their authentication activity.
Prerequisites & Requirements
- You must be a registered URS user in order to perform this configuration.
- You need mod_auth_urs (which you will likely have to build from source; see below).
- You must register a web application and authorize it. See Obtain URS Application Credentials below for more information on this. Note: You can register your application with either the Test URS System or the Main URS System.
- Configure Apache and Tomcat (Hyrax) to work together.
- The public facing domain name or IP address of your server.
Building mod_auth_urs
The documentation for mod_auth_urs describes how to build the module from a clone of the git repo, however we found that on CentOS 6 that process had to be modified to include linking with the ssl library. Since it is a fairly simple build, we'll duplicate it here with the caveat that a newer version of the module might have a different build recipe, so if this doesn't work, check the official page. With that said, to build the module for CentOS 6:
- Make sure you have the httpd-devel and ssl-devel packages loaded onto your host: sudo yum install httpd-devel openssl-devel
- Clone the mod_auth_urs git repo from the ECC system; you need a URS login for this, but you need a URS login for several other steps with this configuration as well: git clone https://<username>@git.earthdata.nasa.gov/scm/aam/apache-urs-authentication-module.git urs
- Build it using he apache extension build tool apxs in the urs directory just made by the git clone command. Note that for CentOS 6 you need to include the ssl library: apxs -i -c -n mod_auth_urs mod_auth_urs.c mod_auth_urs_cfg.c mod_auth_urs_session.c mod_auth_urs_ssl.c mod_auth_urs_http.c mod_auth_urs_json.c -lssl
Obtain URS Application Credentials
- With your browser, navigate to your URS profile page.
- Click the My Applications tab.
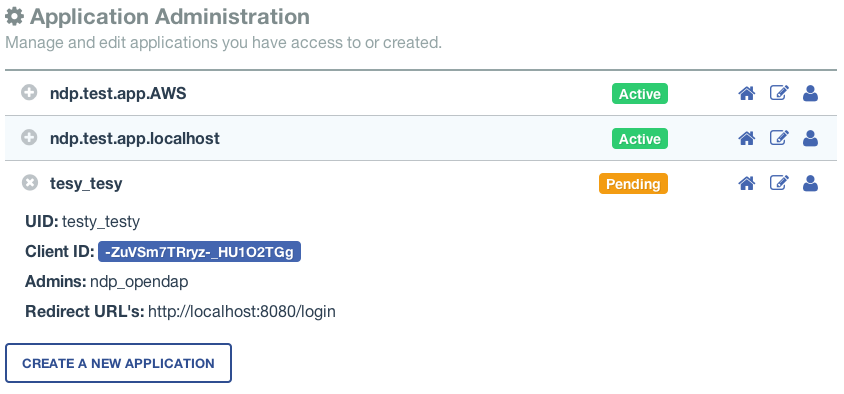
On the My Applications page:
- Click the Create A New Application button.
- Fill out the form and save the information you enter into the form for later.
- Make special note of the application password you submit and the Client ID generated by the URS system.
- Once you have registered the application you'll be able to see it in your profile's My Applications tab.
Its status will show pending a while:
Once your application registration request passes through the approval process in URS land its status will be changed to Active and your instance of mod_auth_urs will be permitted to interact with the URS system. You should get an email acknowledging your application registration and another one indicated your application gas been activated. (The last time I did this it took ~20 minutes to receive the activation notification. ndp (talk))
Approve your URS Application
Once your application marked Active you will need to approve it so that the URS system knows that you are OK with the application having access to you URS user profile information.
Every single URS user that is going to access your new server will need to do this too.
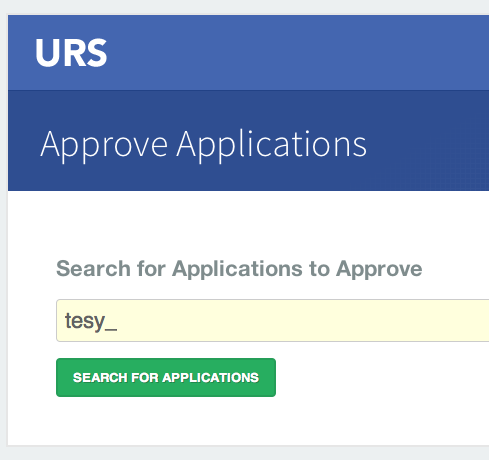
On the My Applications page:
- Click the Approve More Applications button.
This will display the application search page:
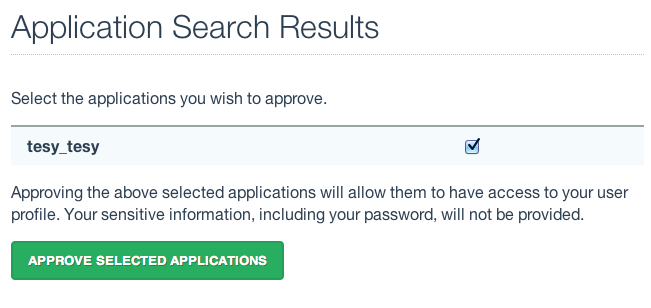
- Enter some or all of the name you picked (which became the UID) of your new application and click the Search For Applications button, this will bring you to the URS Application Approval page:
- Select your new application and click the Approve Selected Applications button.
You will be returned to the My Applications page where you should now see your new application on the list of Approved Applications.
Compute the Authorization Code
The last thing to do before configuring mod_auth_urs is to compute the authorization code for your freshly registered application. To do this you will need to hex encode the ClientID assigned to your application by URS and the password that you assigned to your application when you registered it. The are a number of ways to generate the Authorization Code.
Use a simple perl script:
perl -e 'use MIME::Base64; print encode_base64("<ClientID>:<pw>");'
Or php script:
php -r 'echo base64_encode("<ClientID>:<pw>");'
Or shell script:
echo -n "<ClientID>:<pw>" | base64
Where <uid> is the Client ID for your application that was generated by the URS system and <pw> is the password associated with your freshly registered application. The resulting string of base64 encoded stuff is your application's URS authorization code, aka UrsAuthCode in mod_auth_urs.
Configuration
The instructions for configuring the Apache module mod_auth_urs can be found here:
https://wiki.earthdata.nasa.gov/display/URSFOUR/Apache+URS+Authentication+Module
Notes:
- The instructions are clear and complete but you have to be a registered URS user with permissions to access that page in order to read it.
- Also note that the apxs tool used to build an apache module is part of the httpd-devel package and won't be available if you don't have that package installed.
Once I had it installed all that was need was to create the file /etc/httpd/conf.d/urs.conf and add the configuration content to the file. The configuration file you'll find below is annotated and you will need to review and possible edit the values of the following fields:
- UrsAuthServer
- AuthName
And you MUST edit and provide your application credential information in these fields:
- UrsAuthGroup
- UrsClientId
- UrsAuthCode
- UrsRedirectUrl
And you should review and possibly edit this value to point to an appropriate page on your server for failed authentication:
- UrsAccessErrorUrl
Example urs.conf file for httpd:
# Load the URS module
LoadModule auth_urs_module modules/mod_auth_urs.so
#
# Enable Debugging
# LogLevel debug
#
# START - URS module configuration
# The directory where session data will be stored
#
UrsSessionStorePath /var/tmp/urs/session
#
# The address of the authentication server
# Where you registered your application/server.
#
UrsAuthServer https://uat.urs.earthdata.nasa.gov
#
# The authentication endpoint
#
UrsAuthPath /oauth/authorize?app_type=401
#
# The token exchange endpoint
#
UrsTokenPath /oauth/token
#
#
# END - URS module configuration
# Place a URS security constraint on the Hyrax service
<Location /opendap >
# Tells Apache to use URS/OAuth2 authentication in mod_auth_urs
AuthType UrsOAuth2
# This is a localization field and I think it shows up in
# browser and GUI client generated authentication dialog boxes.
AuthName "URS_AuthTest"
# To access, a user must login.
Require valid-user
##########################################################
# UrsAuthGroup This defines a name for a group of protected resources.
# All resources with the same group will share authentication state. i.e. If a
# user attempts to access one resource in a group and authenticates, then
# the authentication will be valid for all other resources in the group (be
# aware that the group name is also used as a cookie name).
UrsAuthGroup HyraxDataServer
##########################################################
# UrsClientId The Client ID the the URS application registration process
# assigned to your application
UrsClientId ******
##########################################################
# UrsAuthCode You compute this from the Client ID and application password
UrsAuthCode ******
##########################################################
# UrsRedirectUrl This is the redirection URL that was specified when
# registering the application. This should include the scheme (http/https),
# the outward facing domain (host)name (or IP address) of your server,
# the port (if non-standard for the scheme), and path. Note
# that the path does not need to refer to a real resource, since the module
# will intercept it and redirect the user before Apache tries to find a
# matching resource.
UrsRedirectUrl https://localhost/opendap/login
##########################################################
# UrsAccessErrorUrl If the users authentication at the URS service fails,
# this is the page on your server to which they will redirected. If it does not
# they'll get a 404 error instead of the 403.
UrsAccessErrorUrl /urs403.html
UrsIdleTimeout 600
UrsActiveTimeout 36000
UrsIPCheckOctets 2
UrsUserProfileEnv uid URS_USER
UrsUserProfileEnv email_address URS_EMAIL
UrsUserProfileEnv first_name URS_FIRST
UrsUserProfileEnv last_name URS_LAST
</Location>
Assuming that the AJP proxy for Tomcat is already done simply restart Tomcat and Hyrax is ready to be accessed with your URS credentials.
But first...
Tomcat Authentication
Tomcat Authentication Services Configuration
Tomcat provides a number of authentication Realm implementations including the JNDIRealm which provides LDAP SP services for Tomcat. There is currently no Shibboleth realm implementation for Tomcat, and it's an open question for the author if there could be one for Shibboleth or OAuth2 given the way that these protocols utilize 302 redirects away from the origin service.
LDAP
The instructions for configuring Tomcat to perform LDAP authentication are located here. It is clearly a benefit if you understand a fair bit about LDAP before you undertake this.
Here is an example of how to configure Tomcat to use LDAP authentication.
In this example we configure a Tomcat JNDI realm to use the public LDAP service provided by ForumSys.
In the server.xml file we added a JNDI Realm element:
<Realm
className="org.apache.catalina.realm.JNDIRealm"
connectionURL="ldap://ldap.forumsys.com:389"
connectionName="cn=read-only-admin,dc=example,dc=com"
connectionPassword="password"
userPattern="uid={0},dc=example,dc=com"
roleBase="dc=example,dc=com"
roleName="ou"
roleSearch="(uniqueMember={0})"
/>
Configured to work with the Forum Systems test LDAP server.
Then in the opendap web application we added the following security constraint to the WEB-INF/web.xml file:
<security-constraint>
<web-resource-collection>
<web-resource-name>Hyrax Server</web-resource-name>
<url-pattern>/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>user</role-name>
</auth-constraint>
<user-data-constraint>
<!-- this ensures that all efforts to access the admin interface nd resources must use HTTPS -->
<transport-guarantee>CONFIDENTIAL</transport-guarantee>
</user-data-constraint>
</security-constraint>
No changes were made to the $CATALINA_HOME/conf/tomcat_users.xml file.
Shibboleth
There is no actual Shibboleth integration with Tomcat beyond what is provided by running the Apache httpd module mod_shib and connecting Tomcat to httpd using AJP as described in the Apache/Shibboleth section on this page.
URS OAuth2
There is no actual URS integration with Tomcat beyond what is provided by running the Apache httpd module mod_auth_urs and connecting Tomcat to httpd using AJP as described in the Apache/URS section on this page.