DAP: Authentication Discussion: Difference between revisions
| Line 12: | Line 12: | ||
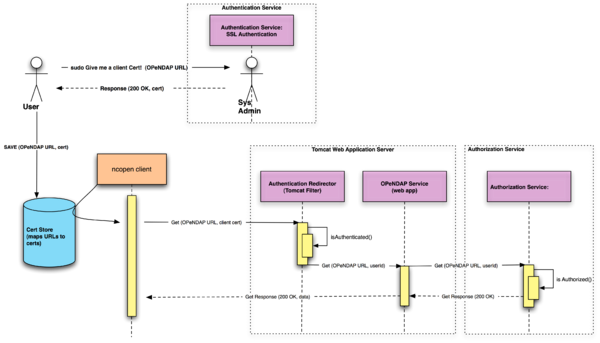
When TLS is used with client certificates the server can easily ascertain the identity of the certificate holder. Thus in a DAP access model if the data service provider issues a client certificate to each user that requires authenticated access the server software can quickly discover who is requesting a particular data holding and pass that information to an authorization service to determine if the requested access is permitted. This authorization service may be as simple as configuring the server to demand a known client certificate to allow access to to some large segment of it's holdings, or it could be a more complex service that details which data granules a particular user may access. | When TLS is used with client certificates the server can easily ascertain the identity of the certificate holder. Thus in a DAP access model if the data service provider issues a client certificate to each user that requires authenticated access the server software can quickly discover who is requesting a particular data holding and pass that information to an authorization service to determine if the requested access is permitted. This authorization service may be as simple as configuring the server to demand authentication (via a known client certificate) to allow access to to some large segment of it's holdings, or it could be a more complex service that details which data granules a particular user may access. | ||
[[File:CertAuth.png|600px|DAP client access over SSL/TLS using client certificates.]] | [[File:CertAuth.png|600px|DAP client access over SSL/TLS using client certificates.]] | ||
Revision as of 17:12, 14 September 2011
Overview
Here we discuss the various candidate technologies for authenticating and authorizing DAP client access to data held in Hyrax or other DAP servers.
SSL/TLS
Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic protocols that provide communication security for network transmissions. SSL was first publicly released in 1995. The technology is mature, proven secure, and is in widespread use through the internet. For the purposes of this DAP discussion we are solely in the versions TLS 1.2 (SSL 3.3) and higher.
This protocol uses an initial handshaking scheme in which the client and the server negotiate a secure connection "in the clear" using public/private key paris. At the end of this handshake both sides of the communication have the information required to compute a "master secret" which is then used to establish a secure communication pathway utilizing a block-cipher. This is a crucial point, as the use of public/private key encryption can very computationally expensive while the block cipher approach is much less so. Here is a sequence diagram describing the TLS handshaking process
When TLS is used with client certificates the server can easily ascertain the identity of the certificate holder. Thus in a DAP access model if the data service provider issues a client certificate to each user that requires authenticated access the server software can quickly discover who is requesting a particular data holding and pass that information to an authorization service to determine if the requested access is permitted. This authorization service may be as simple as configuring the server to demand authentication (via a known client certificate) to allow access to to some large segment of it's holdings, or it could be a more complex service that details which data granules a particular user may access.
One of the very attractive features of the TLS is that it can easily be used for automated programmatic access to data. Once the client certificate has been issued to a user the user can pass that client certificate to multiple web browsers and different DAP client software implementations. The certificate can be used until it expires, or until the data service provider revokes it.